Locally-configured notifiers
Adding a Notifier configuration
Locally-configured notifiers are configured in your config.yaml file under the notifiers field.
Available sourcesToNotify are ALL and SOURCES_IN_THIS_CONFIG, with the default being SOURCES_IN_THIS_CONFIG.
Example config
concurrency: "8"
filterUnverified: true
logLevel: info
notifiers:
- name: stdout secrets notifications
sendUnverified: true
sourcesToNotify: SOURCES_IN_THIS_CONFIG
type: NOTIFIER_TYPE_STDOUT
numWorkers: 16
trufflehogAddress: https://gnarly-flying-pancake.c1.prod.trufflehog.org
trufflehogScannerGroup: account 1 - us-west-2
trufflehogScannerToken: thog-agent-XXXXXXXXXXXXXXXXXXXXXXXXXX
Stdout
notifiers:
- connection:
'@type': type.googleapis.com/notifiers.Stdout
format: JSON
name: stdout secrets notifications
sendUnverified: true
type: NOTIFIER_TYPE_STDOUT
Available formats are PLAIN and JSON, with the default being PLAIN.
Slack
notifiers:
- connection:
'@type': type.googleapis.com/notifiers.Slack
url: https://hooks.slack.com/services/T00000000/B00000000/XXXXXXXXXXXXXXXXXXXXXXXX
name: slack secrets notifications
type: NOTIFIER_TYPE_SLACK
Webhook
Webhook notifiers allow for integrations which subscribe to found secret notifications. When a new secret is found, an HTTP POST payload will be sent to the webhook’s configured URL. Webhooks can be secured by using a token to generate and verify a signature of the payload.
Tokens
The signature is sent using in the X-Hub-Signature header. To verify the signature matches the payload, generate a
SHA256 hash of the payload body prefixed with the token string.
X-HUB-SIGNATURE:5f246d1f78c832eee4d9b453742476a743a1c7fe73454b6b432b26868525423f
> BODY='{"source_type":"SourceType_SOURCE_TYPE_GIT",...}'
> TOKEN="mySecretToken"
> echo -n "${TOKEN}${BODY}" | sha256sum
5f246d1f78c832eee4d9b453742476a743a1c7fe73454b6b432b26868525423f
Payload Body
Filesystem
{
"SourceType": "SOURCE_TYPE_FILESYSTEM",
"Metadata": {
"Data": {
"Filesystem": {
"file": "/Users/hrich/go/src/github.com/org/repo/file"
}
}
},
"SecretType": "Github",
"Secret": "SOMESECRET",
"Verified": false
}
Microsoft Teams
{
"SourceType": "SOURCE_TYPE_TEAMS",
"Metadata": {
"Data": {
"Teams": {
"channelID": "channel-1",
"channelName": "some channel",
"timestamp": "2020-05-01T00:00:00Z",
"userId": "user-1",
"link": "https://teams.microsoft.com/l/message/19:XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX",
"file": "file-1",
"email": "[email protected]"
}
}
},
"SecretType": "Github",
"Secret": "SOMESECRET",
"Verified": false
}
Github
{
"SourceType": "SOURCE_TYPE_GITHUB",
"Metadata": {
"Data": {
"Github": {
"link": "https://github.com/org/repo/blob/XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX/file",
"username": "user-1",
"repository": "repo-1",
"commit": "ae3e9d0f0516d52113386c1e75032536143a241c",
"email": "[email protected]",
"file": "file.txt",
"timestamp": "2020-05-01T00:00:00Z",
"line": 42
}
}
},
"SecretType": "Github",
"Secret": "OTHERSECRET",
"Verified": true
}
Jira
{
"SourceType": "SOURCE_TYPE_JIRA",
"Metadata": {
"Data": {
"Jira": {
"issue": "issue-1",
"author": "user-1",
"location": "https://ourbusiness.atlassian.net/browse/issue-1",
"email": "[email protected]",
"timestamp": "2020-05-01T00:00:00Z"
}
}
},
"SecretType": "Github",
"Secret": "SOMESECRET",
"Verified": false
}
Bitbucket
{
"SourceType": "SOURCE_TYPE_BITBITBUCKET",
"Metadata": {
"Data": {
"Bitbucket": {
"file": "file-1",
"repository": "repo-1",
"workspace": "workspace-1",
"snippetId": "snippet-1",
"title": "title-1",
"commit": "ae3e9d0f0516d52113386c1e75032536143a241c",
"email": "[email protected]",
"link": "https://bitbucket.org/workspace-1/repo-1/src/ae3e9d0f0516d52113386c1e75032536143a241c/file-1",
"timestamp": "2020-05-01T00:00:00Z",
"line": 42
}
}
},
"SecretType": "Github",
"Secret": "SOMESECRET",
"Verified": false
}
Confluence
{
"SourceType": "SOURCE_TYPE_CONFLUENCE",
"Metadata": {
"Data": {
"Jira": {
"page": "page-1",
"space": "space-1",
"version": "version-1",
"link": "http://confluence.example.com/pages/viewpage.action?pageId=page-1",
"email": "[email protected]",
"timestamp": "2020-05-01T00:00:00Z"
}
}
},
"SecretType": "Github",
"Secret": "OTherSecret",
"Verified": true
}
Gitlab
{
"SourceType": "SOURCE_TYPE_GITLAB",
"Metadata": {
"Data": {
"Gitlab": {
"file": "file-1",
"link": "https://gitlab.com/org/repo/blob/ae3e9d0f0516d52113386c1e75032536143a241c/file-1",
"repository": "repo-1",
"line": 42,
"timestamp": "2020-05-01T00:00:00Z",
"commit": "ae3e9d0f0516d52113386c1e75032536143a241c",
"email": "[email protected]"
}
}
},
"SecretType": "Github",
"Secret": "SOMESECRET",
"Verified": false
}
Slack
{
"SourceType": "SOURCE_TYPE_SLACK",
"Metadata": {
"Data": {
"Slack": {
"channelID": "channel-1",
"channelName": "some channel",
"timestamp": "2020-05-01T00:00:00Z",
"userId": "user-1",
"link": "https://slack.com/app_redirect?channel=channel-1",
"file": "file-1",
"email": "[email protected]"
}
}
},
"SecretType": "Github",
"Secret": "SOMESECRET42",
"Verified": true
}
Scanner Configuration
notifiers:
- connection:
'@type': type.googleapis.com/notifiers.Webhook
token: secret_token
url: https://example.trufflesec.com:8081/webhook
name: slack secrets notifications
sourcesToNotify: SOURCES_IN_THIS_CONFIG
type: NOTIFIER_TYPE_WEBHOOK
notifiers:
- connection:
'@type': type.googleapis.com/notifiers.Email
ses:
creds:
key: AKIAXXXXXXXXXXXXXXXX
region: us-west1
secret: XXXXXXXXXXXXXXXXXXXXXXXXXX
recipients:
- [email protected]
sender: <trufflehog> [email protected]
name: email secrets notifications
type: NOTIFIER_TYPE_EMAIL
Splunk
notifiers:
- connection:
'@type': type.googleapis.com/notifiers.Splunk
endpoint: https://splunk.company.com/notify
hecToken: t0ken
isDisabled: true
name: send splunk notifications
type: NOTIFIER_TYPE_SPLUNK
JIRA
The Jira notifier will create a new Jira issue for each found secret. The issue’s summary (title) will include the secret type and source type, and the issue’s reporter will be the user configured to authenticate to Jira. The issue will be created with no assignee.
The value configured as the notifier’s issueDescription will be prepended to a text block that contains the secret type and source type, whether the secret was verified, and additional secret metadata.
Here is a screenshot of a created Jira issue with TruffleHog-generated and user-configured values highlighted:
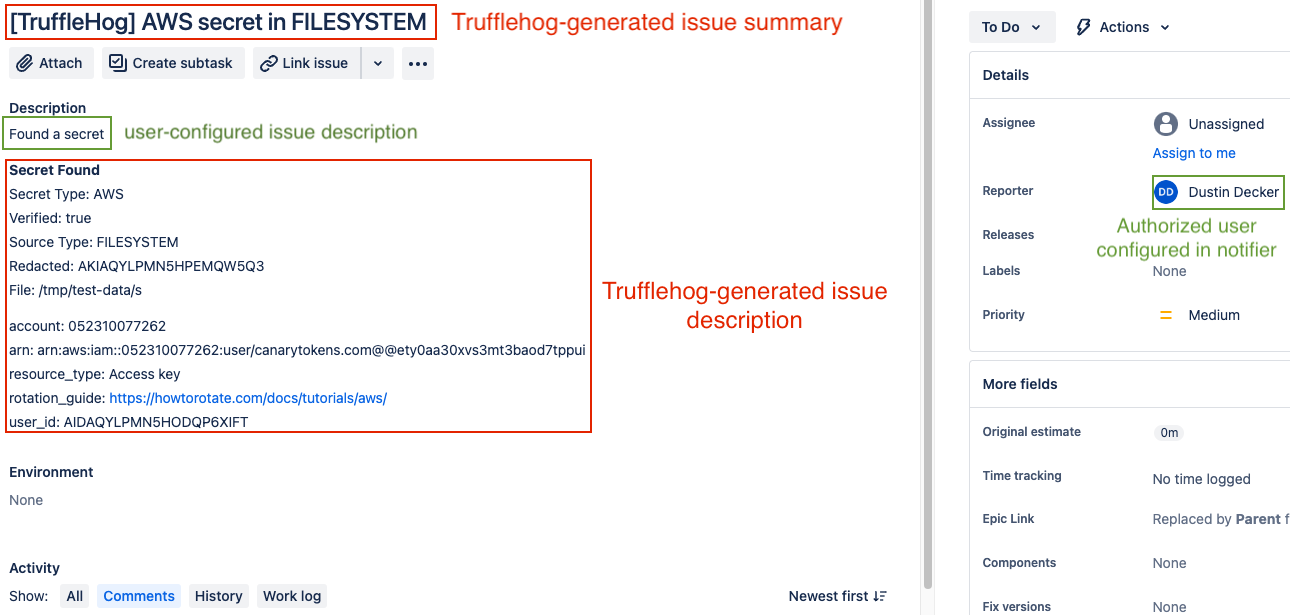
You can optionally configure custom fields for Jira issues if your Jira instance has special fields you want to populate. Available “type"s for CustomField are STRING, NUMBER, and SINGLE_SELECT.
You cannot set the Summary, Description, or Reporter fields as custom fields, as they are automatically set by TruffleHog itself. Attempting to do so will cause errors in the scanner.
TruffleHog will never modify issues in any way after they have been created. In particular, it will not close or update them when it detects that the associated secret has been rotated.
The Jira notifier supports either basic authentication or token-based authentication. If possible, please use token-based authentication as it is the authentication method recommended by Atlassian.
Token-based Authentication
notifiers:
- connection:
'@type': type.googleapis.com/notifiers.JIRA
customField:
- name: CustomField1
type: STRING
value: string field value
- name: CustomField2
type: NUMBER
value: "42"
- name: CustomField1
type: SINGLE_SELECT
value: single select field value
endpoint: https://trufflesec.atlassian.net
issueDescription: Found a secret
issueType: Bug
projectKey: SECRETS
token: PAT
name: create jira tickets
type: NOTIFIER_TYPE_JIRA
Basic Authentication
notifiers:
- connection:
'@type': type.googleapis.com/notifiers.JIRA
basicAuth:
password: t0ken
username: [email protected]
customField:
- name: CustomField1
type: STRING
value: string field value
- name: CustomField2
type: NUMBER
value: "42"
- name: CustomField1
type: SINGLE_SELECT
value: single select field value
endpoint: https://trufflesec.atlassian.net
issueDescription: Found a secret
issueType: Bug
projectKey: SECRETS
name: create jira tickets
type: NOTIFIER_TYPE_JIRA